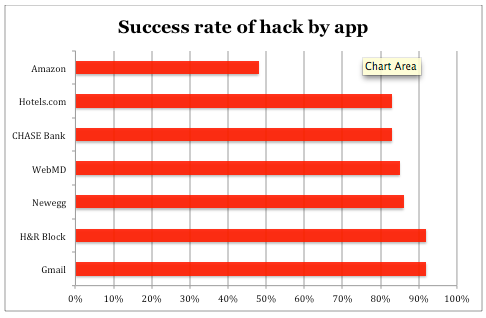
Researchers have found a weakness in Google’s popular Android operating system that let them hack into Gmail accounts with a 92% success rate.
The vulnerability extends to a number of other apps including H&R Block, Newegg, WebMD, Chase Bank, Hotels.com and Amazon, according to their study. In most cases, their technique succeeded 80-90% of the time. Amazon’s app was the most difficult to crack at 48%.
The hack begins when a user downloads malicious software disguised as a seemingly harmless app like background wallpaper app. Next, the masquerading app exploits a common feature of operating systems—shared memory —to figure out what users are doing on their smartphones.
When timed properly—say, just as a user is entering a username and password, or snapping a picture of a personal check—a hacker can launch a phishing attack. Users think they’re punching their passwords into an app like Gmail, Amazon or Chase, but they’re actually typing it into a sham-screen generated by the malicious app.
“At this point, the information is stolen and the attack succeeds,” the authors said in the study. Two of the researchers hail from University of Michigan and another from University of California at Riverside.
In three videos, the researchers demonstrate how to steal login credentials, social security numbers, personal check images, credit card numbers and shipping addresses.
The hack exploits the same design principle that allows alarm and apps that serve as reminder to pop up on a smartphone. Zhiyun Qian, assistant professor at UC Riverside and one of the study’s authors, said in a statement that “by design, Android allows apps to be preempted or hijacked.”
The researchers suspect their method will work just as well on other mobile OS, such as Apple iOS and Microsoft Windows, although they have yet to attempt the hack on those systems. They were scheduled to present their findings today at the USENIX Security Symposium in San Diego.
Google did not immediately respond to a request for comment.